Whether cybersecurity attacks are socially, politically, or financially motivated, no industry is immune. Cyberattacks are targeting financial institutions, military operations, public utilities, and private corporations with rising frequency causing huge revenue losses and extensive damages.
In 2021 cybercrime is expected to cost $6 Trillion globally and as much as $10.5 Trillion by 2025.
Common Threats to Cybersecurity
Cybersecurity threats are deliberate, malicious attempts to gain unauthorised access to a network by either an induvial or an organisation. They aim to corrupt or steal data, extort money from victims, or simply interrupt business operations, and they are becoming increasingly sophisticated. Common types of cybersecurity threats are:
- Malware
- Ransomware
- Distributed Denial of Service (DDoS) attacks
- Spam and Phishing
- Corporate Account Takeover (CATO)
- Unpatched Security Vulnerabilities
- Zero-day Exploits
- CVE (N-Day Attacks)
To protect themselves against the continuous threat of cyberattacks, many organisations are joining or deploying cyber ranges.
What is a Cyber Range?
A cyber range is a platform that provides cybersecurity professionals the ability to practice and strengthen their cybersecurity skills within a secure testbed. The closed environment allows personnel to train against real-world threat scenarios and hone their defenses without posing risk to the production infrastructure.
Since cybersecurity threats are constantly evolving, cyber ranges are an essential tool for standardising training, validating security tools, and keeping cyber defense teams up to date with regular practice and discipline.
By implementing Cyber Ranges organisations are better able to ensure network and application resilience to avoid disastrous data breaches and costly system outages.
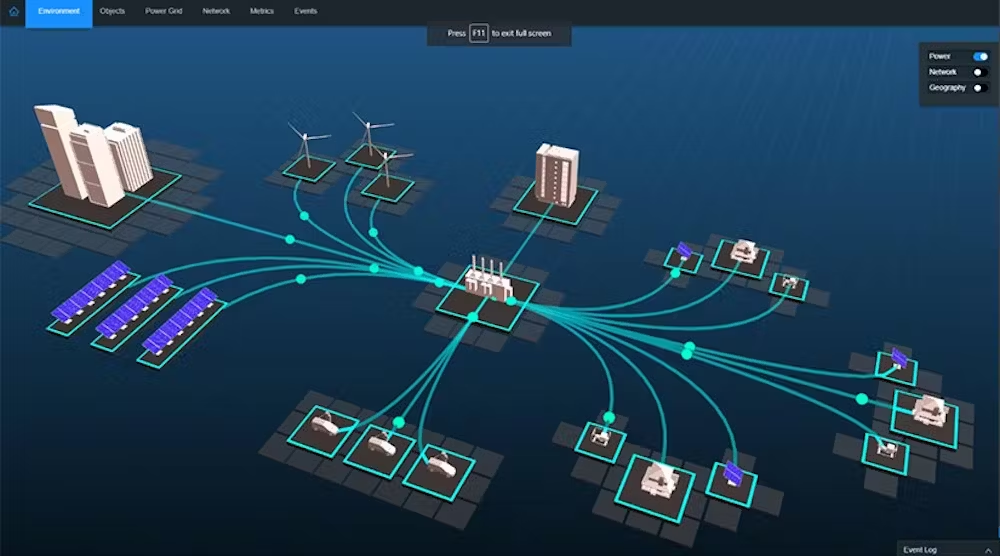
Traffic Generation for Cyber Range Realism
The most effective cyber ranges operate with extreme realism. Not only do the attacks need to be realistic, but the background traffic must also emulate that of a real network. A cyber range should be able to accurately simulate internet connections from around the world, multi-media streams, VoIP, and many other legitimate applications, plus tens of thousands of endpoints attacking the network at once.
Because it is not feasible or scalable to use actual people and computing resources to generate this traffic, Cyber Ranges employ robust application and security test tools like traffic generators.
Traffic generators can emulate a tremendous scale of mixed application traffic and protocols to realistically imitate your organisation’s network or generate potential worst-case scenarios. Traffic generators often come with an extensive library of realistic security attacks, so you can configure malware, zero-day, DDoS, and other attack traffic to come from thousands of unique IP addresses simultaneously.

By incorporating both malicious and authorised traffic into the Cyber Range network, traffic generators allow cybersecurity professionals to train and fight just like they would in the event of a real cyber-attack while providing real-time analysis. The same capabilities are also used to validate that security devices like firewalls are performing as expected.
By designing well-equipped cyber ranges with ultimate realism, organisations are better able to protect themselves against inevitable and ever-evolving cyber attacks.